TL:DR
Objective
Design and build cross-platform web application that provides tools for managing and monitoring sensitive personal information in using decentralized Solid and Inrupt decentralized web servers.
Role
Cross-functional Strategic & Executive Lead Designer
Functions
- Led discovery sessions and design reviews with clients and trusted design partners
- Produced low to high fidelity designs and prototypes
- Designed and managed design library
- Led user-testing efforts
- Provided QA & Testing Support
Timeline
Discovery Phase (single sprint) + ongoing iterative design and development sprints
Objective
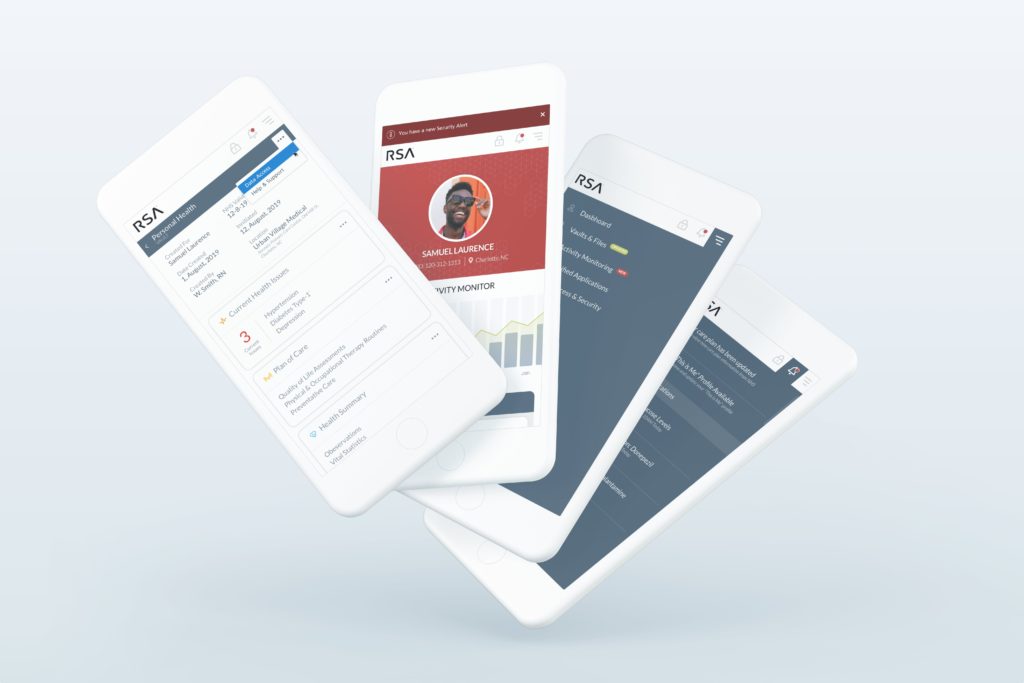
Design and build a secure decentralized data storage tool that:
- Allows users to group like data resources together as needed in specific “vaults”
- Introduces shared access protocols and patterns to securely control sharing of individual files to large swaths of data.
- Is designed and built for decentralized web practices (Linked data, RDF) utilizing Solid Pods
- Interface ensures dynamic cross platform access and usability
- Allows realtime monitoring and security notifications/alerts
Process
Discovery Phase
The discovery phase of the project consisted of the following:
- Goal: Rapidly understand the problems space, proprietary technologies, and synthesize business goals to define requirements and roadmap.
- Results: Conducting initial user research returned that our users do often question the security of their data. However outside of digital credential management, current solutions do little to securely house sensitive private personal information. We moved forward with rapid iterations of concepts and prototypes to test with our trusted partners.
DESIGN PHASE
The iterative design phase utilized the validated user feedback from our discovery phase to validate proposed key features for expected impact; and progress our focus on developing needed product features and to guide our design and development timeline. The application is broken into core segments:
- Decentralized File & Vault Management
- File sharing (Trusted Access)
- Security Alerting/Alarm Notification System
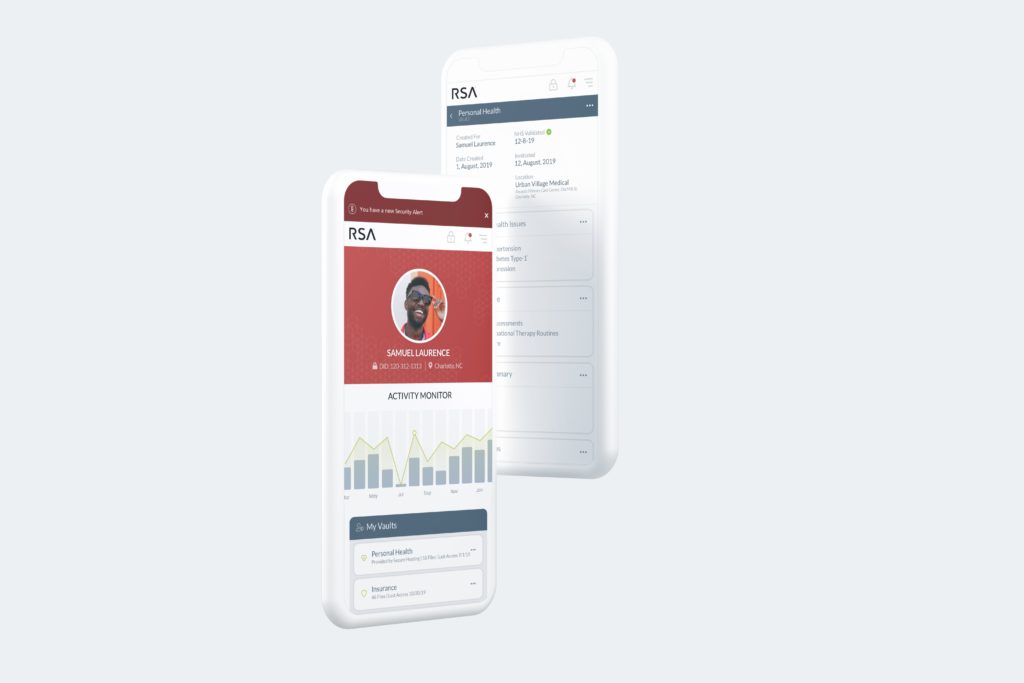
1.0 Decentralized File & Vault Management
Through our user research we found the need to build trust with our user base regarding the concept of a vault and file management within, as well as the need of security even in a decentralized web environment. By pre-provisioning vault placeholders, our test users were able to quickly understand and resonate with vault concept, immediately migrating and organizing data in corresponding categories. All vaults and each file within are continually monitored for access and security issues (via trusted individuals as well as applications/services with access consent).
2.0 File Sharing (Trusted Access)
Granting access and permissions for file sharing in the decentralized web is slightly different from just copying a google drive or box sharing URL. Focused on secure transactions between two users across disparate systems, we utilized multiple factor authentication along with building negotiable consent/grant and rescind access patterns for extending file or vault access to additional individuals.
3.0 Security Alerting/Alarm Notification System
Security today is a 24/7 need, and our users want to be within reach of their security data at all times. That does not mean that they wish to be intrusively notified with every failed access attempt. Thus it became increasingly more important to balance ease of access to security information per file, vault, or access; with a robust alarm notification system to trigger the user to take action if action is needed by the application to secure their files/vaults.